Now that SCOM 2022 is released and available, it is a good time to discuss what is new in SCOM 2022 and what these changes look like.
I am creating an overview here first and where the explanation needs to be more specific and extended, I will create separate pages for those items and link them from here!
SCOM 2022 is the latest version of SCOM in the System Center suite, which also includes other products, such as Data Protection Manager + Service Manager + Virtual Machine Manager and Orchestrator to name a few. This means we see a continued investment in these tools, made to enable you to run, maintain, monitor, backup, deploy, automate large numbers of servers in a datacenter or a private cloud. Assuming the usual support periods, this means a 5 years mainstream support and 5 years extended support again until about the year 2032.
The New Features List
Now, lets talk about what things got added or changed in SCOM 2022.
- Windows Server 2022 now supported to run SCOM Infra components on. Some roles are supported to run on Core servers as well. Others on the desktop experience versions. This is the same as for the previous versions. Windows Server 2022 was of course one of the drivers to come with a new System Center version as well.
- Support for upgrading SCOM 2019 to SCOM 2022. Upgrading one version up is the same as for previous versions of SCOM.
- Enhanced RBAC – Here a Read-Only Administrator role got added to facilitate for example auditors. Also a custom Delegated Administrator role is added whereby you can specify what actions this delegated admin can do within SCOM (for example work with agents, or notifications).
- Alert Closure experience – In SCOM 2019 we had a change where you could no longer close an alert from a monitor which was still unhealthy. Now you have a choice between two behaviors.
- Ability to run tasks under System – There is now a setting to turn off the ability for Operators to run tasks using the predefined action account (which is often SYSTEM) and force them to enter own credentials to run a task.
- Teams notification channel – A new custom notification channel got added which enables you to send out alerts to Microsoft Teams posts in a Teams channel.
- Create SCOM databases on Always-On – This was obviously already there, but it used to take several manual actions after creating the databases to make everything work correctly on secondary nodes in the Always-On cluster. These items have been integrated now in the process.
- Improved install experience – During an upgrade from SCOM 2019 to 2022, a number of registry keys and settings are now retained and moved across to the new SCOM version. Also, if you have installed a SCOM agent in a custom path, the upgrade from 2019 to 2022 agent will keep that path intact.
- Group managed service accounts (GMSA) now supported at RTM. The SCOM 2019 RTM installer did not recognize gmsa accounts, and it took an Update Rollup to be applied first for gmsa to be supported. In SCOM 2022, you can use gmsa straight from the setup wizard.
- Linux agent certificates now get encrypted with SHA256. This strengthens the encryption for these certificates and the encryption for the traffic transferred.
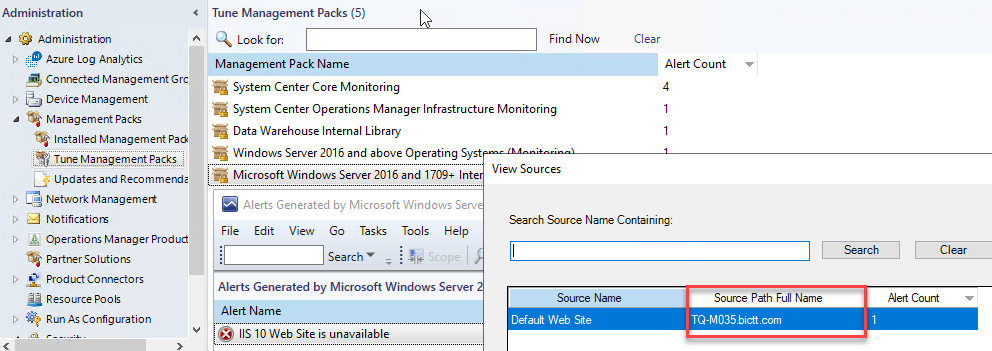
- Alert Source in alerts view – This adds a column to the alerts view which indicated if the alert is coming from a Rule or a Monitor. I am very happy this simple item got added, to make it clear what we are looking at!
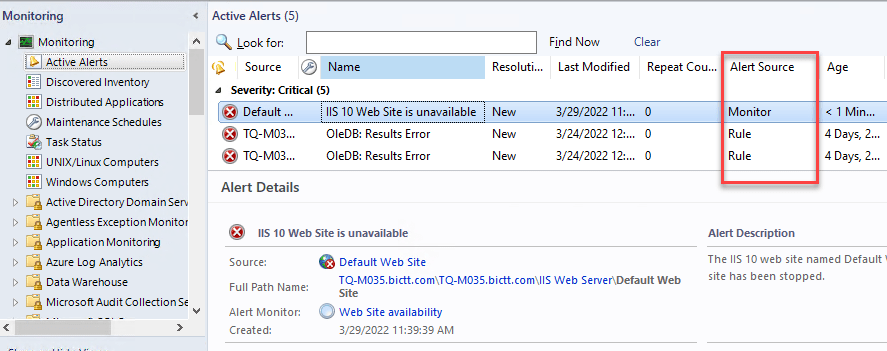
- View alert source in Alert tuning feature – In the SCOM alert tuning feature it was possible to look at which objects caused the selected alert (to find frequent offenders so to say), but given the display name of many similar class objects being the same it was difficult to find the source (path). There is now a field attempting to find the source (such as computer name), making it easier to identify. In the picture below you can see the source name is Default Website, which does not identify where it is running on its own.

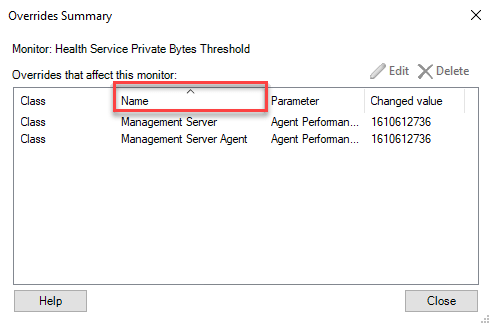
- Sort option in overrides summary views – If you have a lot of overrides on some rule or monitor, it can be difficult to figure out. Adding sorting options makes a longer list of overrides a bit easier to read. It is not just for the column in the picture, but also for other columns you can sort on.

- Getting alert data from REST API now adds groupid as a filter option. This makes it possible to add a filter to collect alerts which come from items in a particular group in SCOM. For example, to get all active alerts from the SQL Computers group. Keep in mind that this uses the internal group name of that group and not the display name.
- Running SCOM Reporting on NTLM hardened systems now possible. This was one of the last SCOM roles which could not run when NTLM was hard disabled. Now it is possible through an install option in the install wizard for SCOM Reporting component (if run on a separate server). It is called Windows Negotiate, instead of the Windows NTLM option in that step of the wizard asking for the Reporting Service Authentication Type.
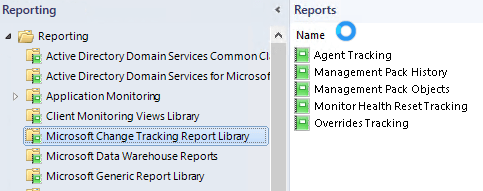
- Change tracking reports moved – the change tracking reports added in SCOM 2019 UR2 and UR3 now got moved to their own folder in the reporting pane.

- Removed dependency on LocalSystem account – this is no longer used internally instead of the default action account. It is still added to SCOM Admins user role by default, but is now visible and can be removed if needed. It was always added by the way in previous versions, but it was invisible through the console.
- Added support for browsers IE11, Edge 88+, Chrome 88+. I highly encourage to use either Edge browser or Chrome browser to view the SCOM web console, if you have it.
- PowerShell 3.0 is now the minimum required version.
- You must install MSOLEDBSQL before you install Operations Manager.
- Added support for .Net 4.8
- Added support for Ubuntu 20, Oracle Linux 8, Debian 10+11 so the newer versions of some of the distributions already supported.
- Removed Support for AIX, Solaris, RHEL5, RHEL6, RHEL7PPC, CentOS6, Debian 8, SLES 11, SLES 12PPC, Ubuntu 16. This does not say you can not get it to work though using a package from the 2019 version for example. So do not get discouraged to upgrade SCOM if you happen to be running one of those distributions listed in this list! It is advisable to test obviously!
- Windows 11 supported for an agent. The rest of the Windows-based agent supported Windows versions is the same as SCOM 2019. Windows server 2022 was already on the SCOM 2019 supported list for agents as well. Windows Agents from Windows server 2012 and up, and Windows 10 and up.
This is the main list of items so far.
Many are self explanatory with a small comment. Some are logical (adding support to Windows 2022). Some can use a little more details and examples or screenshots. For those which require a bit more information, we will create separate blog pages and create a link in the list above per topic.
Happy monitoring!
Bob Cornelissen