One of the items added to SCOM 2022 is an option to disable the use of the predefined run as account for Operators. Let me show you why this happened and what this does!
Previously
In SCOM there are several user roles, such as Read-Only Operators, Operators, Advanced Operators, Administrators and a few more.
When talking about the ability to run tasks in SCOM, the default was that Read-Only Operators could not run tasks and other user levels can. Of course, you could make custom Operator or Custom Advanced Operator and such, and Limit which tasks they could see in their screens. But if a task was visible, they could run it.
When you run a task, you get a popup asking you for credentials.
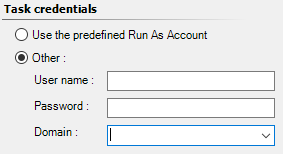
What is advised to do, is to click the Other button and fill in your credentials. So the task will run under your credentials. If this works or not is based on the rights you have on the target system and so on.
However, you could also leave the default selection, at Use the predefined Run As Account. This is the default setting and if you did not bother to enter credentials it would take that option. The good thing about this option is that you could have defined a predefined run as account. For example, the SQL mp has such a run-as profile which is specifically for running tasks. And, as I hope you know, if you did not specify anything in such a Run-As profile, it will default back to the Default RunAs profile. That one contains in most cases the Local System account (not always, but most cases).
The good and the bad
The good part of that is that the task often runs successfully. Local System can run most workflows, if it is not specific to some application, which requires a domain-based account to run. So, the good news is that most Operators in SCOM, could run most tasks in SCOM, due to the use of this predefined account, which is often SYSTEM.
The bad part of this is exactly the same line as above. For security or for organizations with many departments and many Operators, this is not that nice. It enables a user in SCOM at the Operator level (let’s ignore Admin for now), to run tasks as another entity with a lot of rights. On – in most cases – all machines in the SCOM environment.
This caused several organizations to use SCOM less often. Or make heavy use of scoped custom user roles with the tasks all made invisible. Or in some cases (I have seen this) to make all Operators Read-Only. This of course now blocks the ability for an Operator to work with alerts correctly. So, it kind of causes a security measure to be put in place, which causes SCOM to be not used in the optimal way.
SCOM 2022
What got added to SCOM is a new global setting, where you can make a choice. Lets first show the choice.
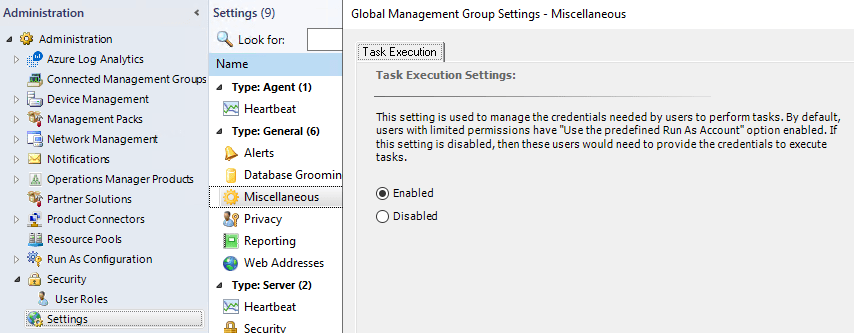
Go to SCOM Administration Pane – Settings – Miscellaneous.
Here you find the Task Execution tab. By default this is set to Enabled, which is basically the same behavior as it was in SCOM 2016/2019.
Now, you can also set this to Disabled. If Disabled is selected an Operator will no longer be able to run a task without entering credentials, because the Predefined run as account option will be disabled. This forces you to have rights on the target system to be able to run a task, which runs on that system. Now, this is something which is in most cases handled in organizations. Where you are in a group with admin rights on a system or for the ApplicationXYZ servers – or not. In which case the task will run or not.
Keep in mind, this setting will apply to SCOM users with limited permissions. SCOM Administrators still see and can use the predefined action account on any task. But Operators can not. I assume the same goes for Advanced Operators and Author roles actually. I have not tested this yet, but infer from the stated text.
Conclusion
So, this will be a relief for several organizations, where giving somebody Operator rights, does not mean some kind of secret workaround SYSTEM elevation (if you happen to know about it, or if you happen to fall on a keyboard and accidentally run some task on a system you should not have). For those organizations, set this setting to Disabled. This forces somebody to type credentials and they either have the rights or not on their own (or own admin-) account.
Back to the overview list for what is new in SCOM 2022!
